Everything / Multimedia / C++
C++
C++
Great Reads
by Michael_Haephrati
Michael Haephrati explains how keyboard capturing should be done
by Michael_Haephrati
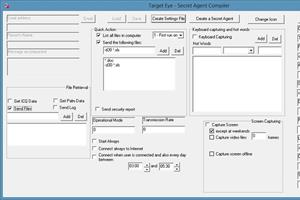
Michael Haephrati describes Target Eye screen capturing mechanism
by Michael_Haephrati
Michael Haephrati describes the Shopping List and how it is used
Latest Articles
by Michael_Haephrati
An example of a small and easy to implement monitoring application
by Michael_Haephrati
Why the creation of a cover story a mandatory part of any covert monitoring product and how Target Eye handled it
by Michael_Haephrati
Michael Haephrati explains how keyboard capturing should be done
All Articles
13 Sep 2013 by Michael_Haephrati
10 Sep 2013 by Michael_Haephrati
13 Sep 2013 by Michael_Haephrati
4 Oct 2013 by Michael_Haephrati
An example of a small and easy to implement monitoring application
4 Oct 2013 by Michael_Haephrati
Why the creation of a cover story a mandatory part of any covert monitoring product and how Target Eye handled it
3 Apr 2012 by LEADTOOLS Support
The benefits of grid and distributed computing are well established and indisputable. However, implementing them can be a nightmare – converting audio/video files in separate chunks can result in video hiccups and out of sync audio – but not with LEADTOOLS!
12 Apr 2012 by Garth Tissington
12 Apr 2012 by Sachin R Sangoi
12 Apr 2012 by Sameers (theAngrycodeR )
12 Apr 2012 by Pascal Ganaye
12 Apr 2012 by Anup Shinde
This article is intended for network administrators and internet users. It shows how users can bypass the firewall to get access to the restricted internet sites. This article is just an overview and does not cover the technical details.
12 Apr 2012 by slw1234@sbcglobal.net
12 Apr 2012 by Lubna Luxmi Chowdhry
Cluster is a term meaning independent computers combined into a unified system through software and networking. Clusters are typically used for High Availability for greater reliability or High Performance Computing to provide greater computational power than a single computer can provide.
12 Apr 2012 by tanvon malik
This article shows you ways to run Control Panel applets from VC++, even those that don't have a cpl extension file.
5 Jun 2012 by Michael_Haephrati
10 Sep 2013 by Michael_Haephrati
12 Apr 2012 by Sameers (theAngrycodeR )
12 Apr 2012 by fraudlabs