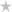- Add AI to your apps
- Learn AI Programming
- Publish your AI projects
Discuss Download Docs
Take a code snippet, simple Python module, a Jupyter notebook
- whatever you're working on - and use CodeProject.AI to turn it into module that can
be deployed and used anywhere by everyone. Learn and play with AI without fighting
tools and setup environments.
Latest Modules
- LLama chatbot on your desktop - CodeProject
- License Plate detection (update) - Mike Lud
- Multi-TPU Coral.AI image detection (update) - Seth
- AI Image generator - Matthew Dennis
- Sound Classification - Chris Maunder
Industry Content
Learn how to deploy an application on a Smartphone
solution to prevent chargebacks and to reduce fraud for online merchants
Explains misconceptions about timing in Windows.
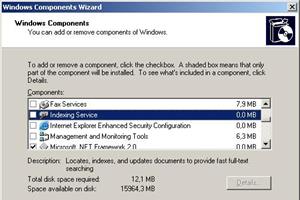
Cluster is a term meaning independent computers combined into a unified system through software and networking. Clusters are typically used for High Availability for greater reliability or High Performance Computing to provide greater computational power than a single computer can provide.
This article looks at all the options available and trades-off each of them for developing a Word add-in. It aims to help the developer choose the best option according to the requirements.
This article is intended for network administrators and internet users. It shows how users can bypass the firewall to get access to the restricted internet sites. This article is just an overview and does not cover the technical details.